Single sign-on (SSO)
Organization master and admins can enable single sign-on (SSO) using SAML 2.0 in the Admin console. Click Admin at the very bottom of the Core menu, and enter the SAML configuration tab. The Admin console will open in a web browser.
SAML 2.0 protocol
Swit offers single sign-on (SSO) using the account information from the Identity Provider (IdP) to sign up and sign in to Swit. SSO allows access to multiple service providers (SPs) with a single sign-on from the IdP. This increases the convenience of Swit users and reduces the risks associated with password loss, thus strengthening organizational security. Moreover, organization administrators can centrally manage members' accounts and access permissions, simplifying management and increasing operational efficiency.
TIP
IdP (Identity Provider), a system that provides, stores, and manages the user's personal information, includes Google Workspace, Microsoft Entra ID (Azure Active Directory), and Okta. In organizations that enabled SSO, members will see options to continue with SSO or sign in with email & password when signing in. Clicking on Continue with SSO will lead them to the sign-in page of the connected IdP.
Configure SSO
To use SSO, first configure your settings in an IdP and continue in the Swit Admin console.
Configure Swit SSO with an IdP
You can configure SSO with an IdP as follows. For Microsoft Entra ID (Azure Active Directory), Google Workspace, and Okta, see here.
-
Visit an IdP you want to configure SSO with.
-
Create a SAML app following the IdP manual.
-
Type in the Entity ID and Reply (ASC) URL as shown below. The labels may vary depending on the IdP.
- Entity ID: https://<<ORG_DOMAIN_NAME>>.swit.io
- Reply URL: https://saml.swit.io/saml/acs
-
Start mapping the attributes you want to integrate to Swit from your IdP.
-
Add the users you want to participate in your organization on Swit to the SAML app.
- Only the users added to the SAML app can sign up and sign in to the organization on Swit via SSO.
- Most IdPs offer an option that requires all users to use SSO. When you use this option, you don't have to add users to each SAML app.
Configure SSO in Swit (SP)
You can configure SSO for your organization in Swit as follows:
-
In the Admin console, select SAML configuration.
-
Select Enable single sign-on with SAML.
-
Copy and paste the following three items from an IdP.
- SAML 2.0 Endpoint (HTTP)
- Identity Provider Issuer (Entity ID)
- SAML Signing Certificate
-
Set other options within the page, and click Save. Authentication will be enabled with your IdP account, so have your account added to the SAML app for the IdP in advance.
Mapping attributes for SSO in Swit
The user attributes used by Swit are defined as follows, and each attribute has a corresponding attribute on your IdP for mapping.
- Labels:
- When the full name is a single attribute:
username - When the first name and last name are distinct attributes:
firstname+lastname
- When the full name is a single attribute:
- The interface description language to use in Swit:
language - Telephone number:
tel - Custom field:
custom:<<CUSTOM_FIELD_ID>>
Match Swit accounts for SSO
When a member attempts SSO, accounts are matched based on the following order:
- If a Swit account is already connected to the IdP account, the account is used to sign in.
- If there is no Swit account that matches the above condition, a Swit account with the given email address will be matched.
- If there is no matching account at all, a new account will be created.
Error code when configuring SSO
- 1150: Invalid SSO URL input. Please re-enter.
- 1151: There is no valid ID provider issued in the SAML response. Please re-enter.
- 1152: Could not verify certificate. Please re-enter.
- 1153: Your account cannot be accessed because it is inactive
- 1157: Invalid SSO username.
- 1158: Invalid SSO name id.
Bind each member's IdP account
For each member to use SSO, their IdP account and Swit account have to be connected with each other. When configuring SAML settings for the first time or changing them, all members of the organization will receive an email asking to connect their accounts for SSO, and when each member attempts SSO for the first time, their accounts are connected.
Send an SSO binding email
For a member to change the IdP account currently connected, organization admins have to send an SSO binding email. You can send an SSO binding email as follows:
- Go to Admin console > Membership > Members & teams.
- Find a member to connect a new email account to, click the See more button, and click Send SSO binding email.
Integration cases by IdP
Below are integration cases for SSO by Microsoft Entra ID (Azure Active Directory), Google Workspace, and Okta. Refer to the IdP you want to set up SSO with.
Microsoft Entra ID (Azure Active Directory)
-
Sign in to the Portal of Microsoft Entra ID (Azure Active Directory), and click Azure Active Directory.
-
Click Enterprise applications, and select All applications.
-
Click + New application, and search Swit to add.
-
In the Single sign-on tab, click SAML.
-
In Basic SAML Configuration under Section 1, enter the below values.
- Identifier (Entity ID):
http://<<ORG_DOMAIN_NAME>>.swit.io - Reply URL:
http://saml.swit.io/saml/acs
- Identifier (Entity ID):
-
When the required fields in Section 1 are filled in, the Edit icon in Section 2 is activated. Click on the pencil icon at the right of User Attributes & Claims, and map with Swit's user attributes following the mapping attributes for SSO in Swit.
-
Unique User Identifier (Name ID)↔user.userprincipalname [nameid-format:emailAddress] -
username↔user.displayname(Required) -
language↔user.preferredlanguage(Optional) -
tel↔user.telephonenumber(Optional)
TIP
When using an app installed from Azure AD Gallery, the above mapping information is already set. You only have to change the items you want changed.
-
-
After finishing all settings, click Save.
-
When SAML is activated, paste the below values on Swit's SAML Configuration page.
- Set up(Section 4) > Login URL
- Set up(Section 4) > Azure AD Identifier
- SAML Certificates(Section 3) > Certificate (Base64)
-
Select Users and groups in the left panel, and add users that will participate in your organization on Swit.
Google Workspace
You can configure SSO in Google Workspace as follows:
-
Enter Google Admin, and click Apps.
-
Click Web and mobile apps.
-
Open Add app, and in the dropdown menu, click Add custom SAML app.
-
In App details, enter App name, which is a required item. Set the Description and App icon, which are optional, if needed. After finishing the setting, click CONTINUE.
-
The SSO URL, entity ID, and certificate, which are information provided by the IdP Google Workspace are displayed. Copy each information and enter Swit Admin console > SAML Configuration to paste the information to SAML 2.0 Endpoint (HTTP), IdP Issuer (Entity ID), and SAML Signing Certificate, respectively, and click CONTINUE.
-
In Service provider details, enter the below information for ACS URL and Entity ID.
- ACS URL:
https://saml.swit.io/saml/acs - Entity ID:
https://<<ORG_DOMAIN_NAME>>.swit.io
- ACS URL:
-
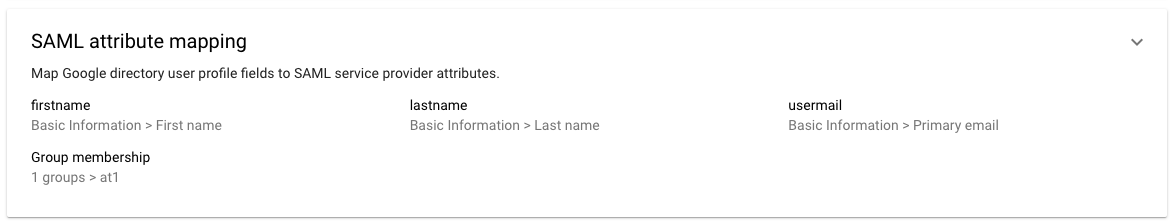
In the Attribute page, click ADD MAPPING and enter the mapping attributes for integration with Swit.
- Basic Information >
Primary Email↔useremail - Basic Information >
First Name↔firstname - Basic Information >
Last Name↔lastname
- Basic Information >
-
After entering the above mapping values, click FINISH to complete SAML configuration with Google accounts.
-
In the Service provider details page, change the settings of the Name ID as follows to configure SSO:
- Name ID format: PERSISTENT
- Name ID: Basic Information > Primary email
-
In User access, select the groups to allow access to your organization in Swit. Choosing ON for everyone will allow all users access.
Configure SSO in Okta
You can configure SSO in Okta directory as follows:
- Enter Okta and sign in as admin.
- In the Applications tab, select Applications.
- Click Create App Integration.
- Select SAML 2.0, then click Next.
- In General Settings, which is the first stage, enter the app name and other options, and click Next.
- In Configure SAML, the second stage, conduct the following activities:
- a. In General, enter the values below to set SAML.
- Single sign on URL:
https://saml.swit.io/saml/acs - Audience URI (SP Entity ID):
http://<<ORG_DOMAIN_NAME>>.swit.io
- Single sign on URL:
- b. In Attribute Statements (optional), enter the mapping attributes, click Next, and click Finish.
- a. In General, enter the values below to set SAML.